Every organization should perform routine security audits to ensure that data and assets are protected. With growing cyber attacks, it's very important for any organization whether small, medium or large, government/semi-government/private to have regular IS Audit. Single cyber attack can not only cause monetary loss, reputational damage which was built over years but also may lead to legal issues for not taking care of vulnerabilities in the system.
IWM audit process includes a comprehensive vulnerability and risk assessment, security posture assessment, and assessment of security controls implemented across organization's information systems. Based on the scope of testing, we can provide following approaches:
Types of Penetration Testing
-
Black Box Testing
-
IWM team will act like a hacker with no information about infrastructure.
-
-
Grey Box Testing
-
Some information about the infrastructure will be provided to the IWM team.
-
-
White Box Testing
-
IWM team will be completely aware of infrastructure.
-
We provide various methodology based audits
Risk Assessment
Penetration Testing
Vulnerability Assessment
Compliance Audit

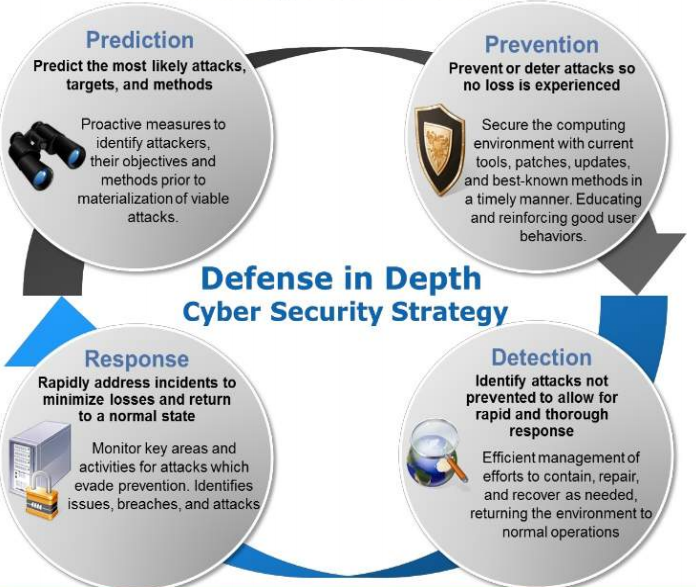
"Enterprise Security Assessment" is an exhaustive audit where we follows Defense-In-Depth strategie.We are very flexible and based on our customers' requirements, we can customize scope of IS Audit. We can do an audit of any of the mentioned assessments. We also helps our customers to setup BCP (Business Continuity Plan) and DRP (Disaster Recovery Plan).